June 4, 2018 | Digital Marketing, Power BI
With technology advancing at an unprecedented pace today, it has become essential for corporations to ensure optimal security when sharing confidential corporate reports and other such information. atQor offers consulting services for the Microsoft Power BI platform, so you can get the perfect solution to your business data analysis and sharing needs.
What is MS Power BI?
Simply speaking, the Microsoft Power BI platform allows you to share, provide access, and secure reports and dashboards created by you with other authorized users only. This is the efficient way today of providing limited/complete access to users, depending on the level of their role.
The Microsoft Power BI security system is the perfect tool to improve your business performance. It allows you to create analytics, and get a deeper insight into your market, to make smart, profitable business decisions. With the Power BI platform now, you can achieve the optimal level of data security in sharing sensitive corporate dashboards and reports like never before.
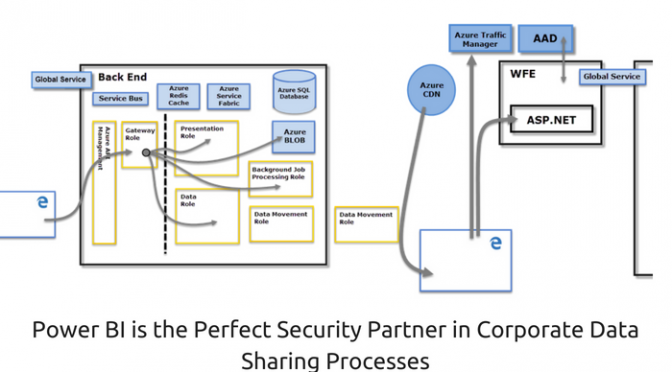
The Security in Power BI Structure
Each Power BI system consists of two clusters:
Salient Benefits of using Power BI Security
These are the top three benefits that are seen when you employ MS Power BI for corporate data storage, access, and security purposes:
Secure Data Storage
The restricted direct user-access through Power BI is probably the best security feature in this service suite. The Power BI security procedure allows users to interact directly only with the Gateway Role and Azure API Management, while the rest of the aspects of Power BI, such as Presentation Role, Data Role, Background Job Processing Role and Data Movement Role are out of the user’s reach.
Any form of data sent to the Power BI storage is stored and managed using two different components:
This clear demarcation for user accessibility to the different components of the Power BI allows it to effectively keep all user data and corporate information stored in MS Azure safe and completely secure.
Excellent User Authentication
The AAD (Azure Active Directory) is used by the Power BI for authenticating users as soon as they log in, as well as when requesting access to any data or content in the storage. A simple email address is needed to login to the Power BI services, as this inherently becomes your Username on the system too.
Apart from this excellent authentication procedure, the Power BI security platform also allows adding customized AAD-based security protocols, enhancing multi-tenant system security and improving your network security effectively.
Successful Service Security
Normally, users are responsible for sharing data. If a user logs in with their effective Username and shares any content (dataset, dashboard, etc) they are connected to within the specific data source, the shared data is not restricted by conventional restriction measures.
Only connections with SQL Server Analysis Services, through On-Premises Data Gateway, can cache dashboards in Power BI. If the user wishes to allow access to other users to the underlying data, then such authentication can also be granted.
atQor has been a prominent provider of Microsoft, especially the Azure cloud-based services globally. The company is renowned for offering the best and most effective IT solutions for small and large corporate clients.